
Hey everybody,
Now that the Umbral Choir has snuck their way onto the Steam store ahead of Endless Day, it’s time to reveal the secrets of these mysterious intruders to the Endless Galaxy and the new feature they have brought with them.
Invisibility
As shadowy, immaterial beings, the Umbral Choir show an aptitude for deception, and the other factions of the galaxy must catch up by necessity. Any faction can now equip their ships with new support modules that allow them to Cloak, which renders them invisible to enemy sensors and lets them slip past blockades, but also stops them from establishing a blockade, sieging, or many other fleet actions. However, they can still attack, catching the enemy off guard, and in fact some Cloaking modules are specialized for combat!
To counter this unseen threat, you can also equip your ships with Detection modules that will reveal cloaked enemy fleets, if your Detection power matches the power of their Cloaking. More advanced Detection modules will allow you to drop Detection Probes on systems, which will maintain their Detection level indefinitely even if the ship leaves, though they can be destroyed.
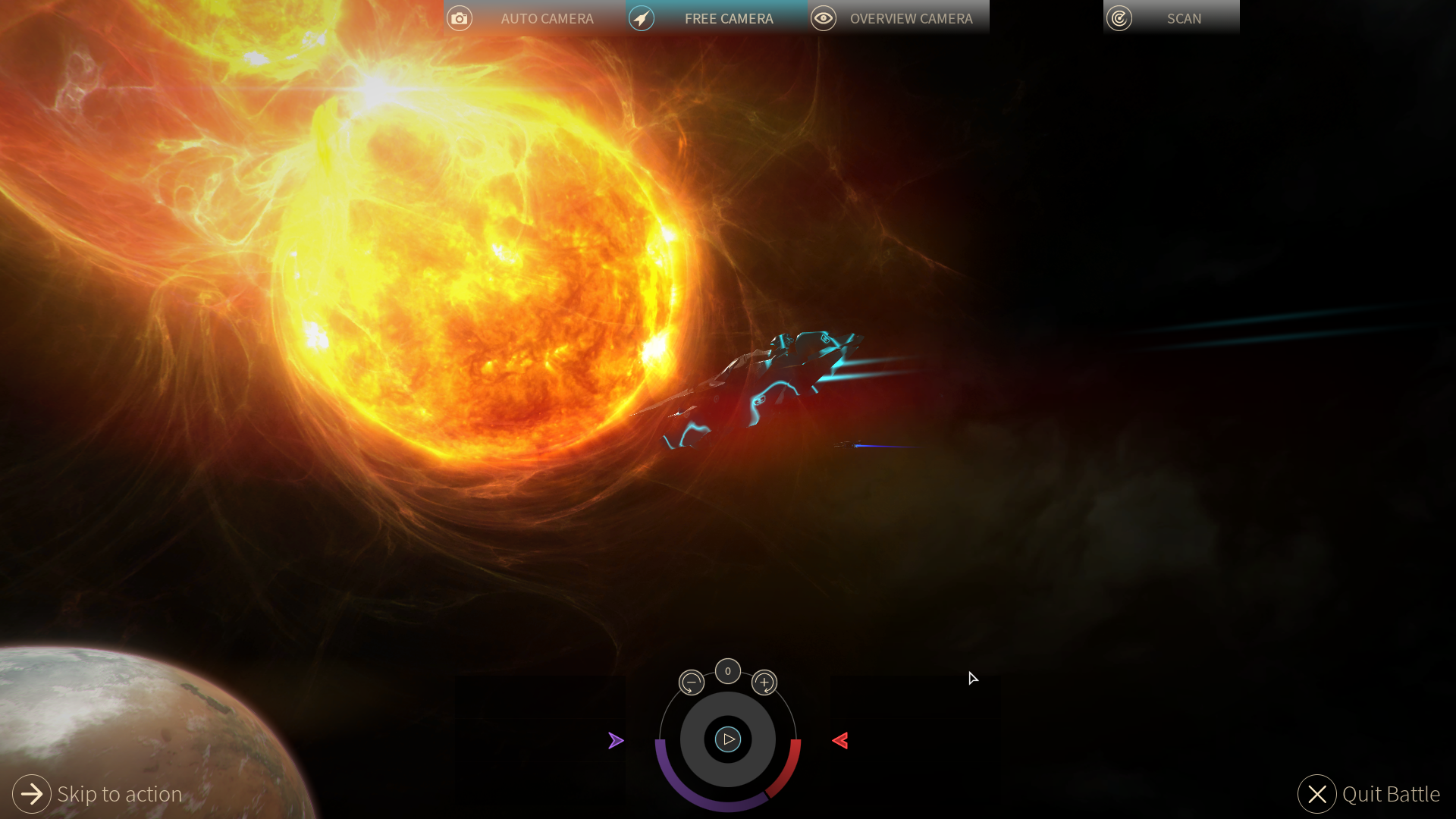 A cloaked Umbral Choir ship entering combat
A cloaked Umbral Choir ship entering combat
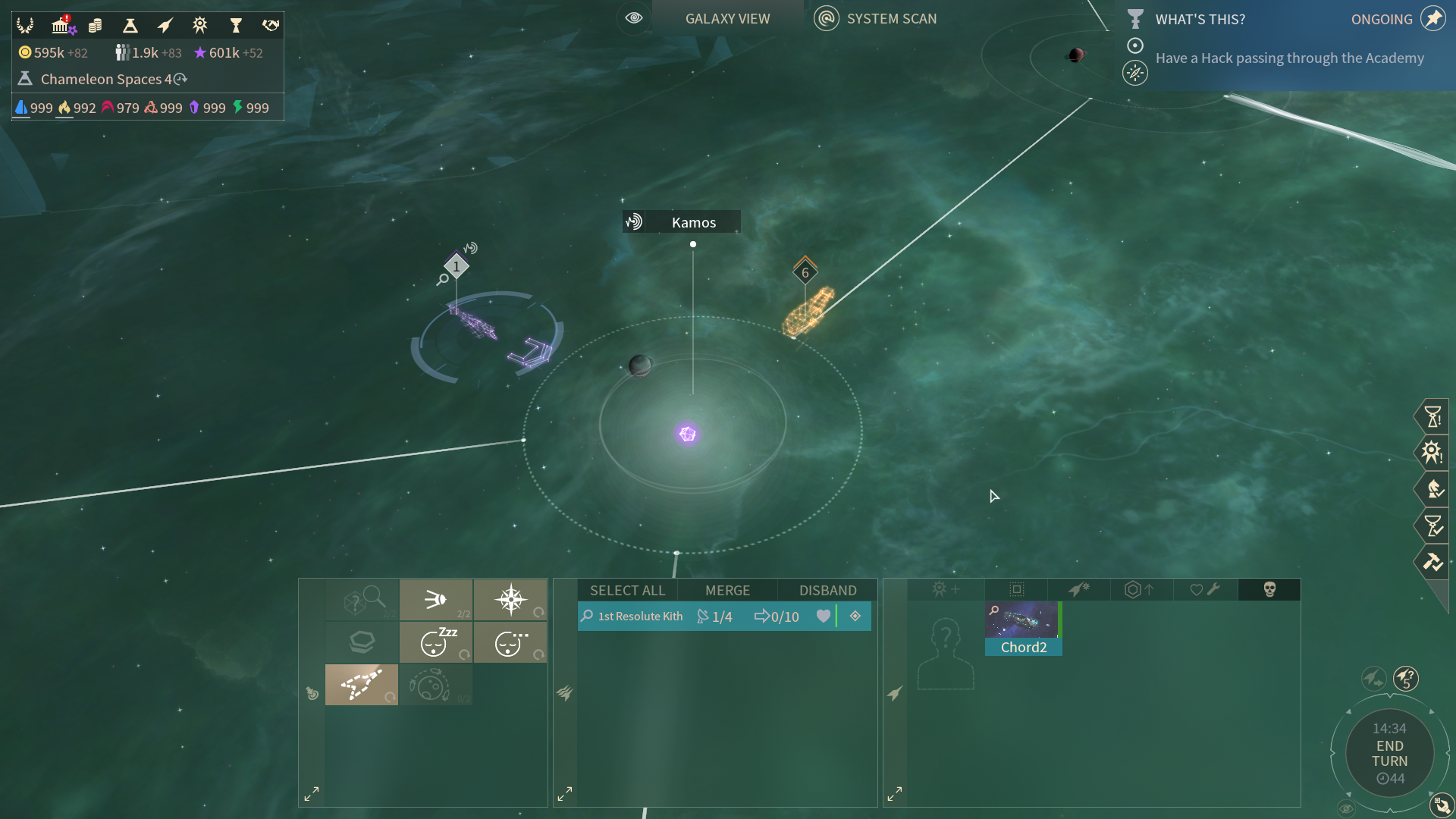 A scout with Detection module and a Detection Probe
A scout with Detection module and a Detection Probe
Hacking
Given that in Endless Space 2 we are dealing with entire systems home to many billions of people, sending a single spy would be little more than an inefficient gesture (unless perhaps we are talking about our good friend Rhync). Luckily, information networks are ubiquitous and Faster-Than-Light communications readily available, opening a new venue for our covert operations: Hacking.
You can hack pirate lairs, minor faction systems, or enemy systems by entering the scan view, selecting a system you own as the origin of the hack, and picking a target. Once you have confirmed your hacking operation, it will proceed along hyperlanes or through space every turn until it reaches a node, which it will need to hack to progress along its path or apply effects.
To aid in your hacking endeavors, you can also place Offensive Programs on nodes along the path of your hack, which will boost your hacking speed, allow you to divert to a different target, or many other effects, or Defensive Programs on your own nodes that will improve your protection. However, all these programs need to be maintained, and that requires Bandwidth. If you run out of Bandwidth, some of your programs will get cancelled. However, programs can not be cancelled manually once they have been triggered, so plan ahead accordingly if you don’t want to lose a critical component of your master plan.
If your hack encounters an enemy defense program, it will trigger a Security Breach, and the enemy will begin to trace you. A trace will follow the path your hack has taken back to its source, but it will always progress faster than a hack would. If the trace reaches the source of your hack before your hack finishes, your hack will be canceled, and you may suffer harsh consequences on the system where the hack originated. You may even find yourself unable to control that system for a few turns!
However, if your hack is successful, you will have access to a variety of outcomes: For example, you can sabotage pirate fleets or steal their loot, discredit a minor faction’s suzerain, steal sensor data or technology, start revolutions, or embed sleeper agents in enemy empires!
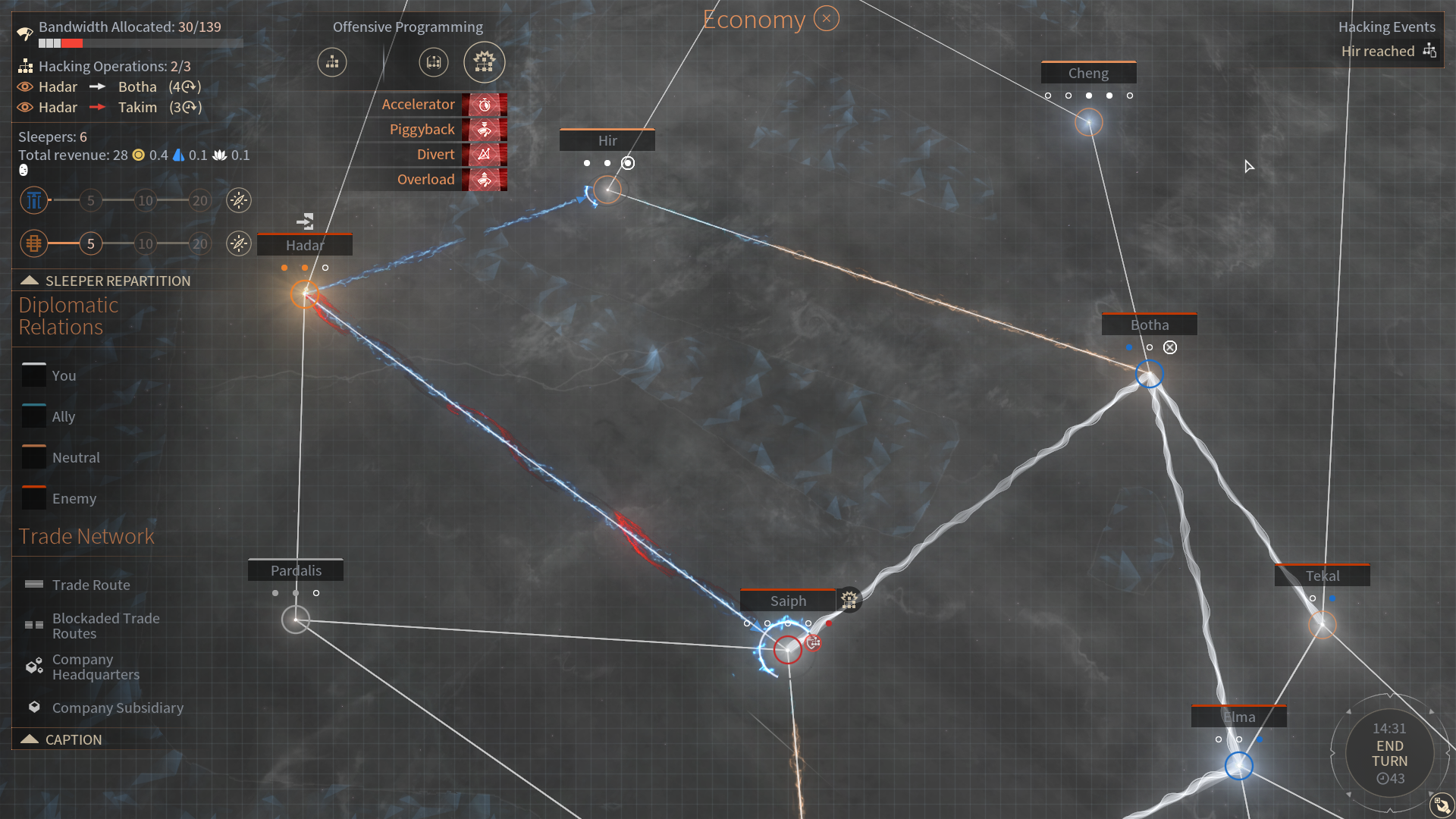
The Hacking Interface
The Umbral Choir
Alien to the Endless Galaxy, the Umbral Choir interact with its systems and people in unique ways. They have made their home in a special node by creating artificial planets called Crescents, which are difficult to detect for other empires. In other systems, the Choir do not establish traditional outposts and colonies, but instead hack the planet to create an invisible Sanctuary for their population to inhabit and transfer its resources to the home system. These Sanctuaries cannot grow or produce anything on their own, but they can coexist with the colonies of other empires – often unknown to them.
This cohabitation of systems allows the Umbral Choir to quickly turn the population of other empire into unwitting Sleeper agents, redirecting some of their Dust and Resource income to the Craver Veterans’ Fund Umbral Choir. When the time is right, the Choir can hack or invade the system to abduct their Sleepers and transform Umbral Choir population of their home system to an Umbral Shadows, doubling their resource output!
Other empires may not be happy about you stealing their Dust, resources, and even people, but luckily your presence is well hidden from their prying eyes. All your fleets can be Cloaked without having to equip a module, your Sanctuaries are invisible, and so is your home system. If an enemy does manage to detect The Nexus, you can hack any special node to migrate your home system, though this can be risky!
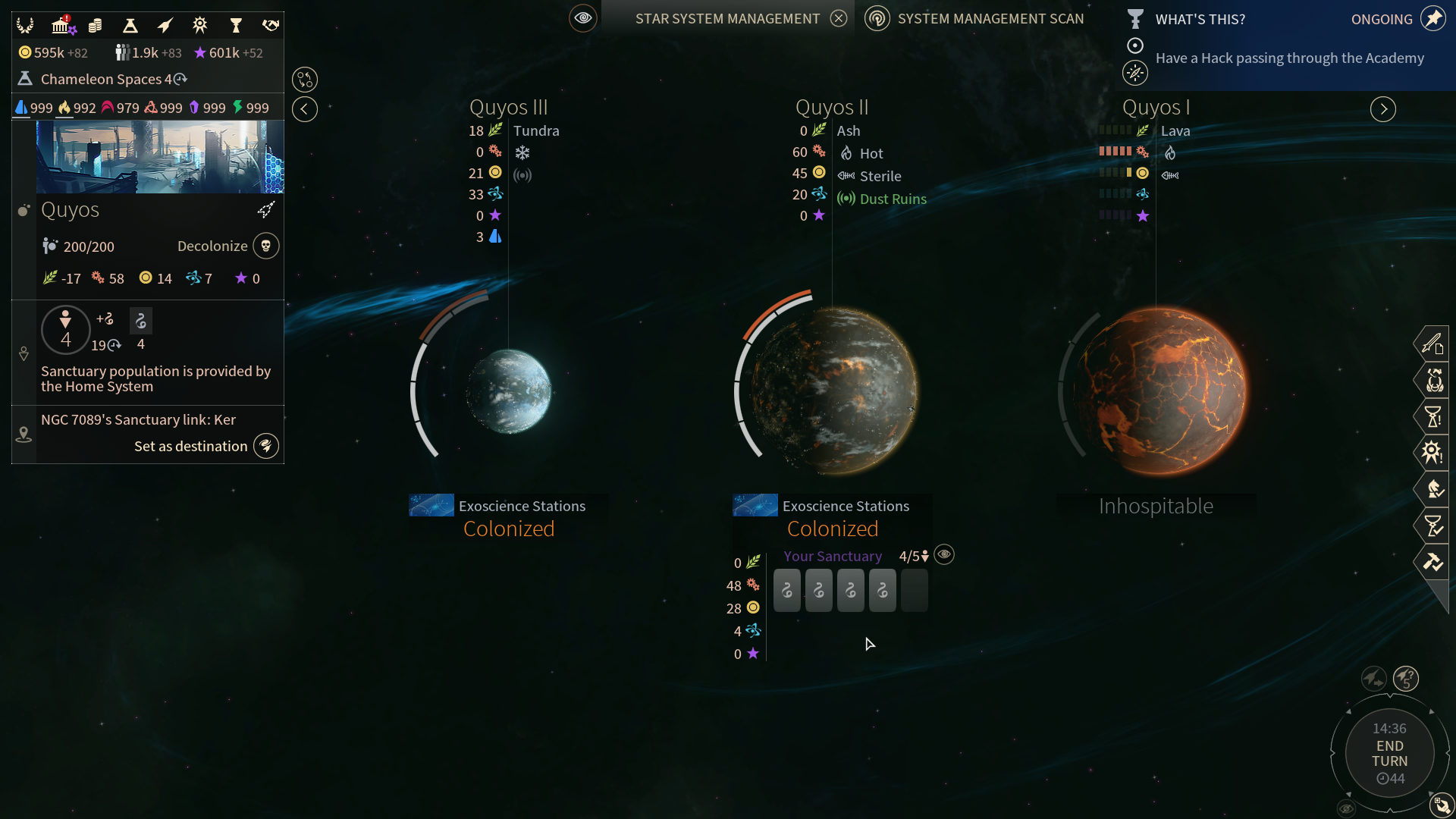
A Sanctuary on an enemy planet
We hope you'll enjoy this take on espionage, but don't get caught!



